U.S. Marshals Service Hit by $40M+ Insider Theft: Government Custody Breach Exposes Risks of Centralized Asset Management
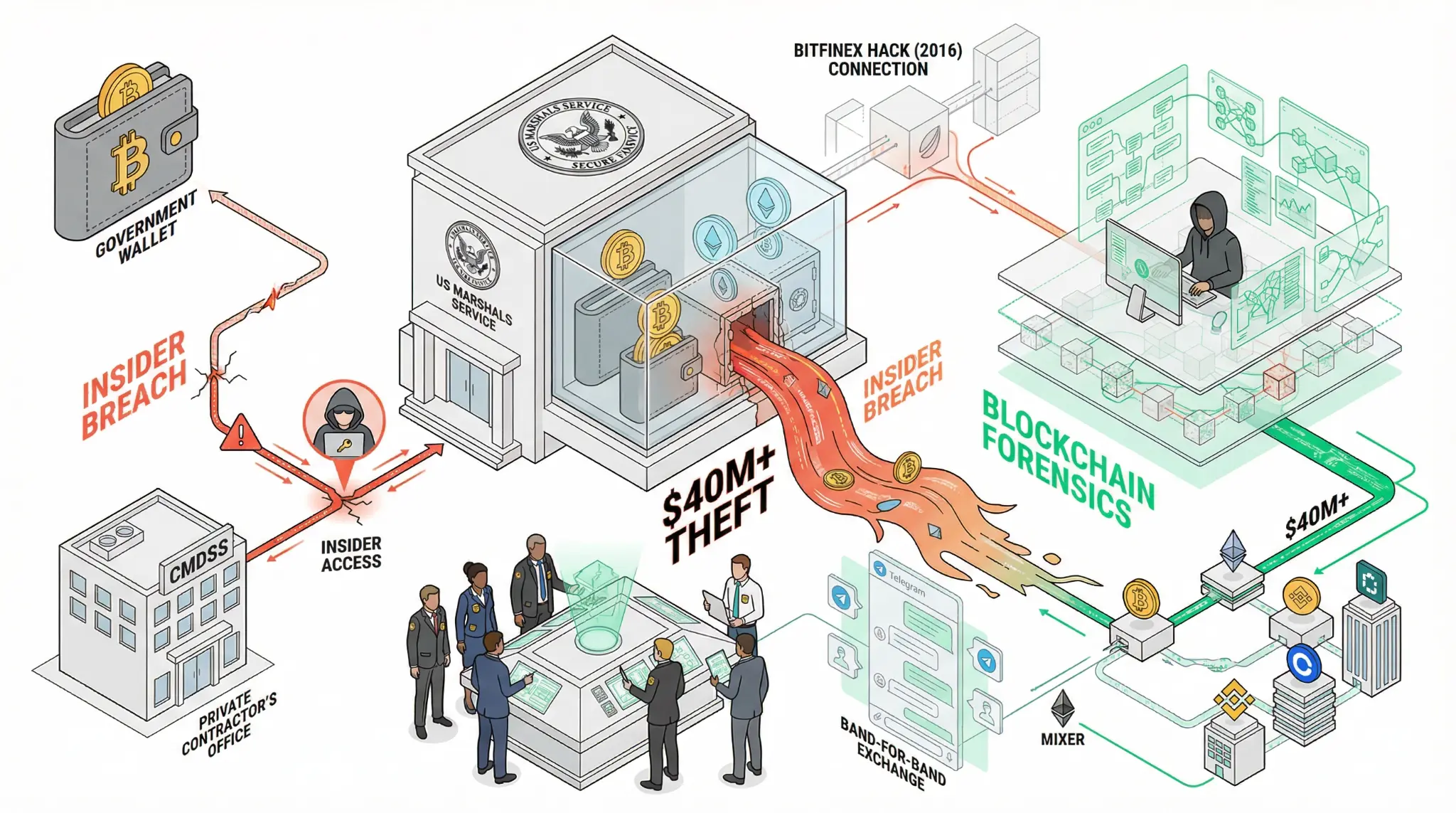
January 26, 2026 - In a stunning security breach that has exposed critical vulnerabilities in how governments manage cryptocurrency holdings, blockchain investigator ZachXBT has uncovered evidence of an alleged $40 million-plus theft from US Marshals Service wallets, with the total suspected illicit activity potentially exceeding $90 million [1]. The investigation traces funds from a US government-controlled wallet containing seized assets from the 2016 Bitfinex hack to wallets attributed to an individual allegedly related to an executive at Command Services & Support (CMDSS), a Virginia-based firm contracted by the US Marshals Service to assist with custody and disposition of seized cryptocurrency [1].
This is not a theoretical vulnerability; this is a real-world breach that has already resulted in the loss of tens of millions of dollars in government assets. The breach exposes a fundamental tension in the cryptocurrency ecosystem: while blockchain technology is often praised for its security and transparency, the human element—custody, access control, and insider threats—remains a critical vulnerability. When a government agency entrusts its cryptocurrency holdings to a private contractor, it is introducing a point of failure that can be exploited by insiders with access to the system [1].
"The public exposure of alleged control over such assets is highly unusual; historically, investigations of this scale rely on covert tracing, exchange cooperation, and prolonged legal processes rather than voluntary disclosure. This case underscores a recurring reality of blockchain investigations: even sophisticated laundering operations can unravel through overconfidence, public exposure, or operational error. Immutable on-chain records allow investigators to reconstruct complex financial activity over time, even when value moves across multiple chains and services." - TRM Labs [1]
The investigation began on January 23, 2026, when ZachXBT publicly disclosed findings linking a pseudonymous crypto user known as "John" or "Lick" to more than $90 million in suspected illicit cryptocurrency activity. The attribution was made possible by an unusual circumstance: a "band-for-band" exchange on Telegram, where crypto participants attempt to prove relative wealth by displaying and moving cryptocurrency holdings in real time. During this exchange, the user known as "Lick" screen-shared an Exodus wallet displaying a TRON address holding approximately $2.3 million. Over the course of the interaction, an additional $6.7 million in ether was transferred live into an Ethereum address. By the end of the exchange, roughly $23 million had been consolidated into a single wallet [1].
Because the transactions occurred live and were accompanied by screen-sharing, ZachXBT was able to directly observe address control, transaction hashes, and wallet consolidation behavior, enabling high-confidence attribution. This is a remarkable example of how blockchain's transparency can work against those attempting to hide illicit activity. The immutable nature of blockchain transactions means that once assets are moved on-chain, they leave a permanent record that can be traced and analyzed [1].
| US Marshals Theft Investigation Metric | Figure | Significance |
|---|---|---|
| Alleged Total Theft | $40M+ (possibly $90M+) | Massive government asset loss. |
| Bitfinex Seizure Funds Traced | $24.9 million | From government-controlled wallet to suspect. |
| October 2024 Anomalous Activity | $20 million drained | Majority returned within 24 hours. |
| Unrecovered Funds (Oct 2024) | ~$700,000 | Routed through instant exchanges. |
| Wallet Consolidation (Jan 23) | ~$23 million | Live consolidation during Telegram exchange. |
| Alleged Suspect Connection | John Daghita / Dean Daghita (CMDSS President) | Unverified allegations. |
| Contractor Status | CMDSS awarded USMS contract Oct 2024 | Custody and disposition of seized crypto. |
| Investigation Status | No criminal charges announced | Allegations remain unverified. |
Tracing the consolidated wallet activity backward, ZachXBT identified flows originating from a US government address that received seized funds from the 2016 Bitfinex hack. Specifically, one upstream transaction showed a transfer of approximately $24.9 million from a government-controlled wallet in March 2024. ZachXBT had previously flagged anomalous activity involving that government wallet in October 2024, when approximately $20 million was drained. The majority of those funds were reportedly returned within twenty-four hours, though roughly $700,000 routed through instant exchanges was not recovered [1].
The laundering patterns observed in the investigation are consistent with known techniques. Funds moved from victim and seizure-linked addresses into intermediary theft wallets, where value was split, recombined, and cycled through multiple hops. Assets were routed through a combination of centralized exchanges, non-custodial services, decentralized exchange infrastructure, and cross-chain swap mechanisms, consistent with efforts to introduce liquidity and obscure provenance before reconvergence [1].
ZachXBT alleged that the wallet controller may be related to an executive at CMDSS, a firm contracted by the U.S. Marshals Service to assist with custody of seized digital assets. Company records confirm Dean Daghita serves as president of CMDSS. However, ZachXBT emphasized that these claims remain allegations and should be treated as unconfirmed pending further evidence or official action [1].
For traders, quants, and investors, the US Marshals theft has several important implications. First, it exposes the risks of centralized custody arrangements for government cryptocurrency holdings. Second, it demonstrates that blockchain's transparency can be a double-edged sword—while it enables investigators to trace illicit activity, it also means that any breach of custody is immediately visible on-chain. Third, it raises questions about the security practices of government agencies and private contractors managing cryptocurrency assets. Fourth, it suggests that as governments accumulate larger cryptocurrency holdings, the insider threat risk increases.
The breach also has implications for the broader adoption of cryptocurrency by governments and institutions. If government agencies cannot securely manage their own cryptocurrency holdings, how can they expect citizens and businesses to trust them with larger amounts? This could accelerate the adoption of decentralized custody solutions and self-custody practices, which eliminate the insider threat by removing the need for a trusted third party.
References
[1] ZachXBT Uncovers Crypto Theft Network Linked to US Government Seizure Funds
